Ransomware continues to be one of the most serious and disruptive cyber threats. The business models, motivations, and infection techniques of emerging campaigns have diversified, and new strands of ransomware continue to outpace the release of decryption tools. By 2019, global ransomware damage costs are expected to surpass $11.5 billion per year.
The three most memorable ransomware campaigns of 2017 - Wannacry, NotPetya, and Bad Rabbit - were ground-breaking in their scope, spread, and destructive power, demonstrating that every business, industry, and country is a potential victim. Although the damage caused by these attacks highlighted the importance of good cyber hygiene, many companies have struggled to address even the most widely reported vulnerabilities. As prevention is better than cure, this article will discuss some of the most common infection vectors and how the Darktrace Enterprise Immune System can assist security teams in catching ransomware threats.
Motivations: financial gain or wreaking havoc?
Ransomware is traditionally linked with making a quick buck by getting the victim to pay a set fee to unlock encrypted files. The phenomenon of ransomware-as-a-service has made this easier than ever before, as it has allowed virtually anyone to purchase ever more potent ransomware distribution kits on the Dark Web. The recent growth in cryptocurrencies has also made maintaining anonymity much easier than before, resulting in a definite increase in financially motivated cyber-criminals.
Regrettably, the goal of ransomware is no longer just to make money. NotPetya and other campaigns such as Ordinypt were designed to purposefully destroy data instead. Even though NotPetya provided its victims with payment instructions, it had no way of identifying who had actually made the payment. The uncertainty surrounding the recovery of lost files and the possibility of being associated with funding malicious organizations have therefore deterred many victims from meeting the ransom demands.
No matter how much a business tries to safeguard their assets, incidents are inevitable, and ransom attacks are an increasingly likely choice of criminal action. But it is now possible to identify in-progress attacks and handle them before they become a crisis.
Case Study 1: Executable file download from a compromised website
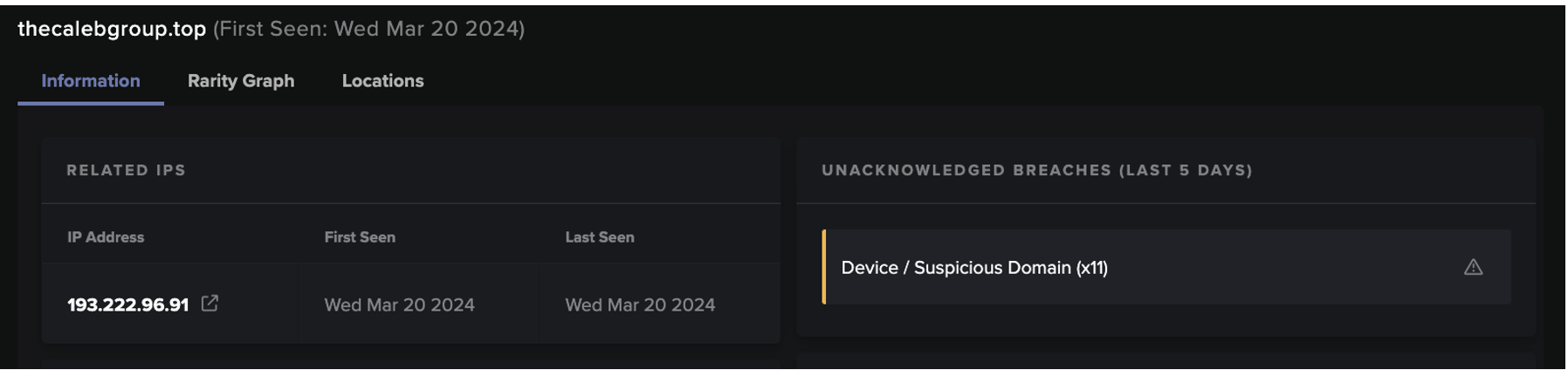
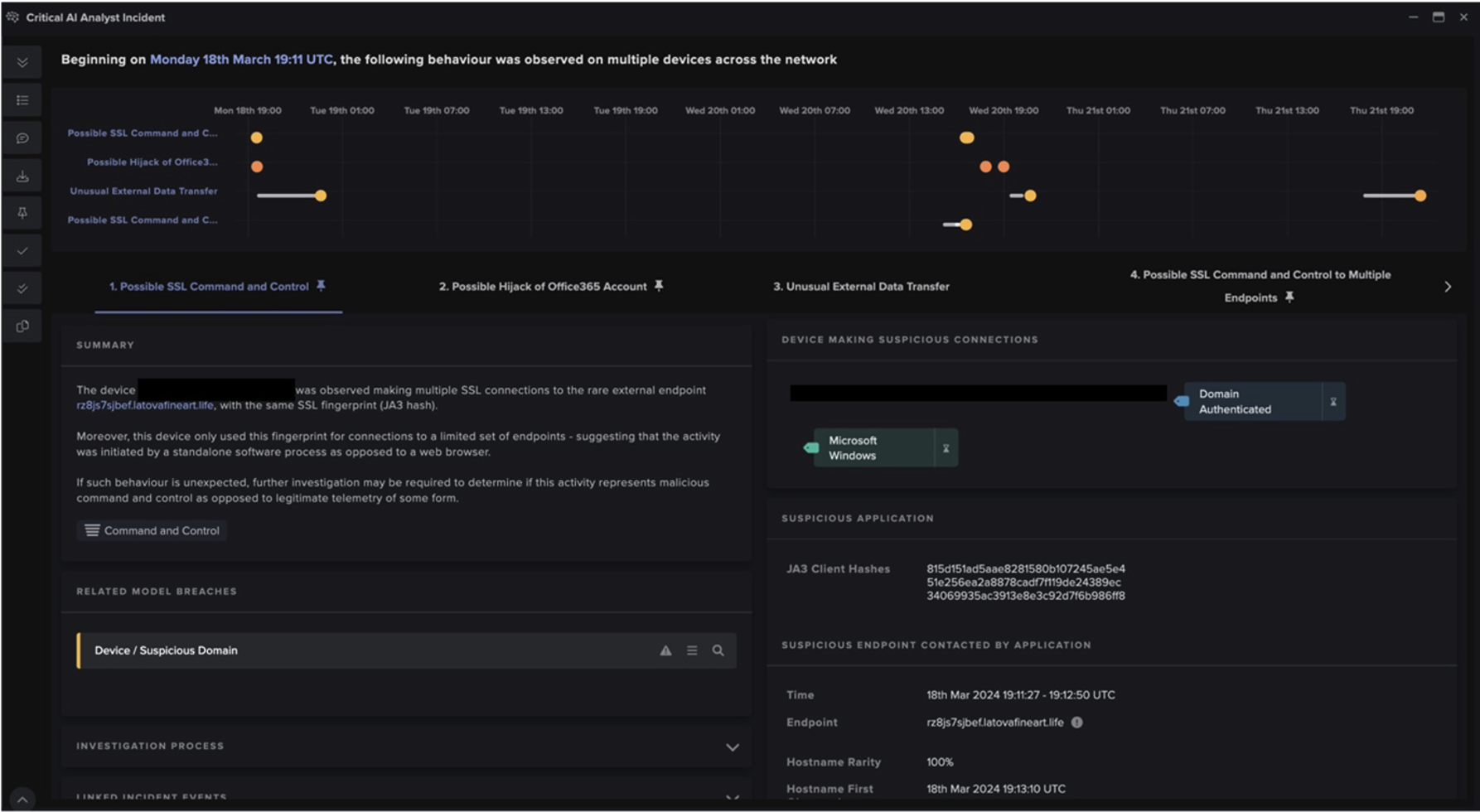
Many prolific ransomware strands have been distributed by phishing emails, infected file downloads, compromised websites, malvertising, and exploit kits. In many cases, ransomware is often downloaded and installed without the victim’s knowledge. To illustrate the ransomware download mechanics, we will analyze the life-cycle of a GandCrab incident. In the case study detailed below, the Darktrace Enterprise Immune System flagged a customer device retrieving an executable file from a previously unmonitored location following a redirection from another rare site.
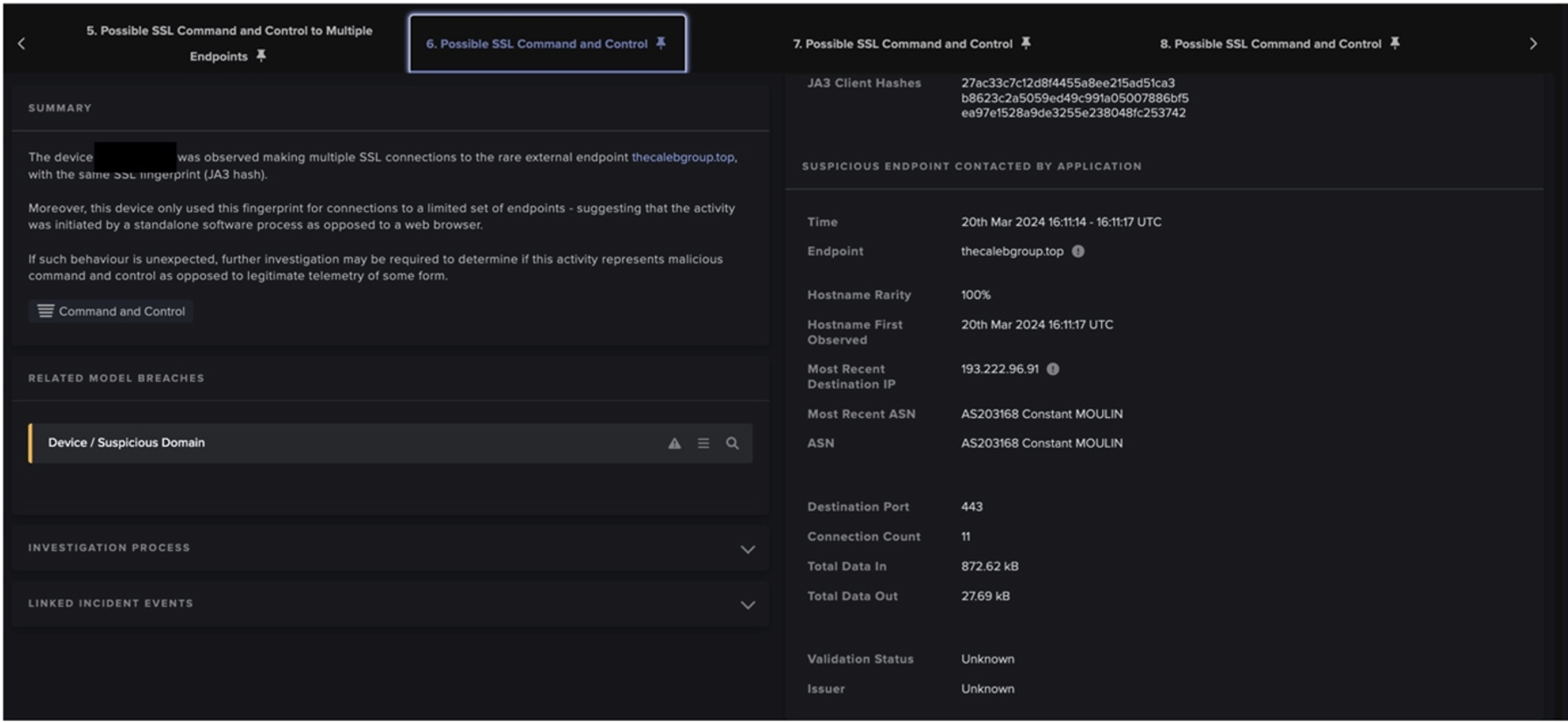
The file containing ransomware was downloaded from a website registered to a Polish domain. Shortly after downloading the file, the customer’s device began reaching out to two locations which had not been contacted by any other network devices, nomoreransom.bit and bleepingcomputer.bit. Both are command and control servers for GandCrab ransomware. Once contacted, the malicious virus proceeded to encrypt files on the SMB server, adding the .GDCB (GandCrab) extension as it moved through the folders.

The virus modified the original file extensions in the encryption process.
Within seconds of the virus appearing on the company’s network, the Darktrace Cyber Analyst team alerted the security team of the threat. Preventative action was then taken, which allowed the threat to be contained within a timely manner.
Case Study 2: Bruteforcing Remote Desktop Protocol access
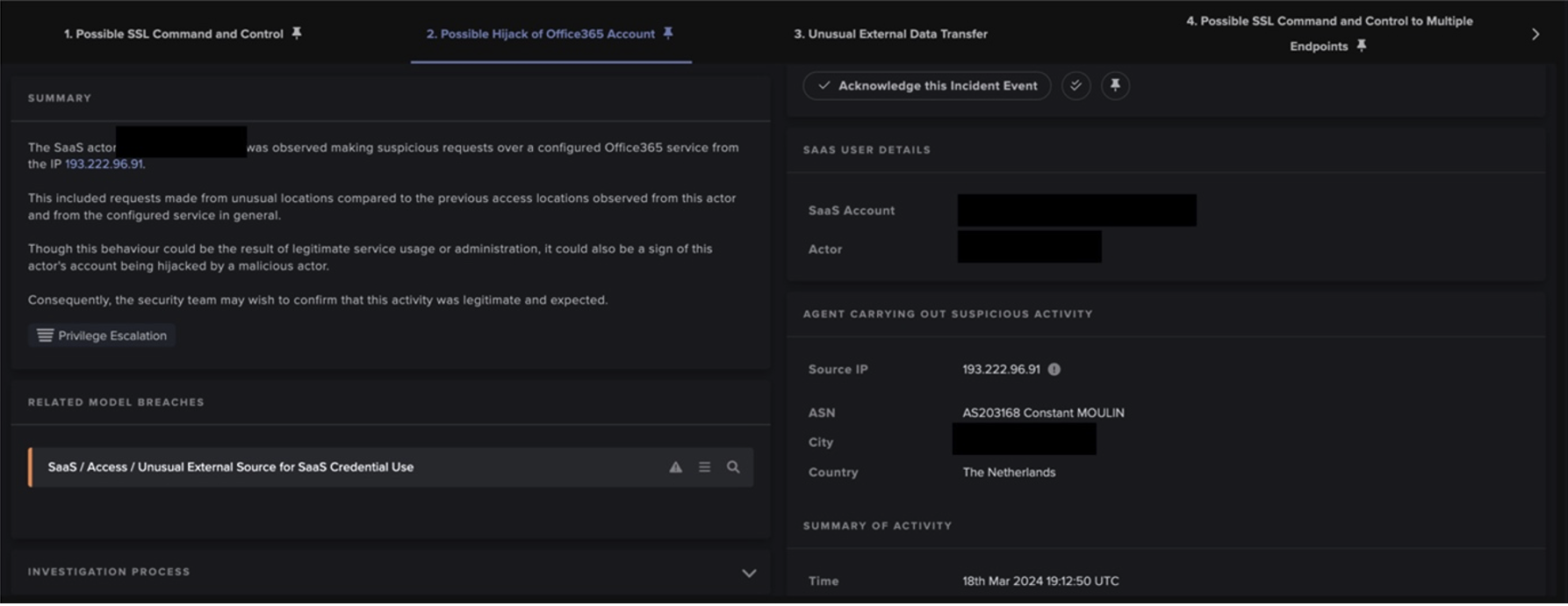
In addition to devising clever ways of downloading ransomware onto victim’s machines, some hackers have turned to bruteforcing Remote Desktop Protocol (RDP) access instead (HC7 & Lockcrypt). Exposing Remote Desktop services to the Internet is risky, as attackers can force access into a network by guessing login information and remotely exploiting a range of possible vulnerabilities and administrative tools in order to infect other available machines.
In another particularly serious breach, Darktrace detected a series of suspicious activities indicating that a malicious actor had taken control of a key server and was using it as a pivot point in order to move laterally throughout the network and install Remote Access Tools (RATs) on multiple devices.
In the initial stage of the attack, the Darktrace Enterprise Immune System observed over 400,000 incoming connections on a port that was targeting devices with RDP turned on and immediately flagged the first signs of a bruteforce attack.

Over 400,000 incoming RDP from multiple rare external devices.
The attack was successful; a compromised server was then used to retrieve malware that granted backdoor access and scanned the network for devices with open RDP channel. The hacker subsequently tunneled through the intermediary, gained control over multiple other machines, and installed third-party remote access software to all available devices.
Although most RDP bruteforcing incidents the Darktrace Enterprise Immune System observes do not escalate this far, the Darktrace Cyber Analyst team are constantly flagging instances of publicly accessible remote management services. To prevent ransomware that specifically exploits insecure RDP configuration, businesses should move these critical services to a virtual private network. Moreover, with Darktrace Antigena, Darktrace’s autonomous response solution, businesses can benefit from an added layer of protection. In this case, it would have blocked any anomalous RDP connections to the server, thus preventing any lateral movement throughout the network.