A Thin Margin for Error
The airline industry has long been known for its thin profit margins, and the high costs of unexpected downtime. 2010’s Eyjafjallajökull eruption in Iceland and the resulting six-day airspace ban across Europe cost airlines $1.7 billion, just a taste of the impact that would come ten years later as a result of the pandemic. The industry collectively amassed more than $180 billion in debt in 2020, and some predictions suggest that by 2024 the industry's debt could exceed its revenue.
Given the impact that further sustained downtime could have on an already ailing industry, airlines are having to take cyber security seriously. Last year’s Colonial Pipeline ransomware attack in the US led to a six-day shutdown of pipeline operations – the same length of time that flights were grounded by the Eyjafjallajökull eruption. But while the industry hasn’t seen a volcanic eruption on that scale in over twelve years, ransomware attacks are striking airlines weekly. Just this year a ransomware attack on SpiceJet left hundreds of passengers stranded at airports across India, despite being contained relatively quickly.
Fraud, Fines and Safety Risks
It isn’t just ransomware which is concerning many in the industry. Data breaches remain one of the biggest threats to airlines, organizations which are responsible at any one time for the personal and financial information of millions of customers. In 2019, British Airways had the data of 380,000 customers stolen, including addresses, birth dates and credit card information, and was fined £20 million (reduced from £183 million due in part to the impact of the pandemic) by the UK’s Information Commissioner’s Office (ICO), the largest issued fine in the ICO’s history. The European airline EasyJet is currently facing a class-action suit seeking £18 billion in damages after failing to properly disclose the loss of 2,208 customers’ credit-card information in 2020.
Airlines are also losing out to card and air mile fraud, with thousands of fraudulent loyalty program accounts being sold on the dark web, as well as the usual roster of attacks including phishing and insider threats which affect businesses of every size and industry. The airlines themselves are not being complacent. In a 2021 report by SITA, 100% of airlines surveyed named cyber security as a key investment for the next three years. Making sure that those investments count will be the next challenge.
There are few industries for which safety and security measures are so important, and while no impact on flight safety as a result of a cyber-attack has yet been reported, agencies like Eurocontrol are already urging caution. Airlines and airports should look at smarter ways to proactively protect their digital environments.
As attacks grow faster and less predictable, organizations are increasingly turning to preventative AI security measures. For airlines, which operate with broad attack surfaces and plenty of valuable data, using tools which can identify and monitor every asset and potential attack path in an organization and take the necessary steps to secure them is the best way to stay ahead of attackers.
Securing Airspace, Securing Cyberspace
As a recreational pilot myself, I understand the extent of the safety measures that go into every flight: the flight plans, pre-flight checks and all of the long-practiced, deep-embedded knowledge. It is this comprehensive and meticulous approach which ought to be reflected in organizations’ cyber security efforts – whether they be airlines, airports or any other type of business. The parallels between the processes of flying and running a digital organization safely give us a helpful way to understand what proper, AI-driven cyber security can do for any organization, airlines included.
Cleared for Takeoff
For the pilot, safety measures start long before they’re sat in the cockpit. Flight planning, which includes planning heading and bearing, taking things like elevation, terrain, and weather conditions into consideration, must be completed in addition to plenty of pre-flight checks. The checklist the pilot works through when performing a walk around and pre-flight inspection will often be ordered so that they work in a circle around the perimeter of the whole plane. These checks prevent potential threats, covering everything from water having mixed with the fuel to birds making nests inside the engine cowling.
Darktrace PREVENT, released in July 2022, serves a similar purpose. The AI autonomously identifies and tests every single user and asset that makes up a business in order to spot potential vulnerabilities and harden defenses where necessary. Like a walk around, PREVENT/Attack Surface Management examines the full range of external assets for threats. Then, by identifying and testing potential attack pathways and mitigating against weak points and worst-case scenarios, PREVENT/End-to-End takes steps to win the fight before an attack has been launched.
Maintaining Good Visibility
When you’re piloting a plane, first and foremost you need a way to detect key variables. Your fundamental flight instruments in the cockpit are known as the six pack:
1. Airspeed Indicator
2. Attitude Indicator or Artificial Horizon
3. Altimeter
4. Turn Coordinator
5. Heading Indicator
6. Vertical Speed Indicator
These six instruments provide the critical information needed by any pilot to safely fly the aircraft. While additional instruments are required to conduct flights In low-visibility or ‘Instrument Meteorological Conditions’ (IMC) conditions, these will be essential when getting out of dangerous situations such as inadvertently flying into cloud.
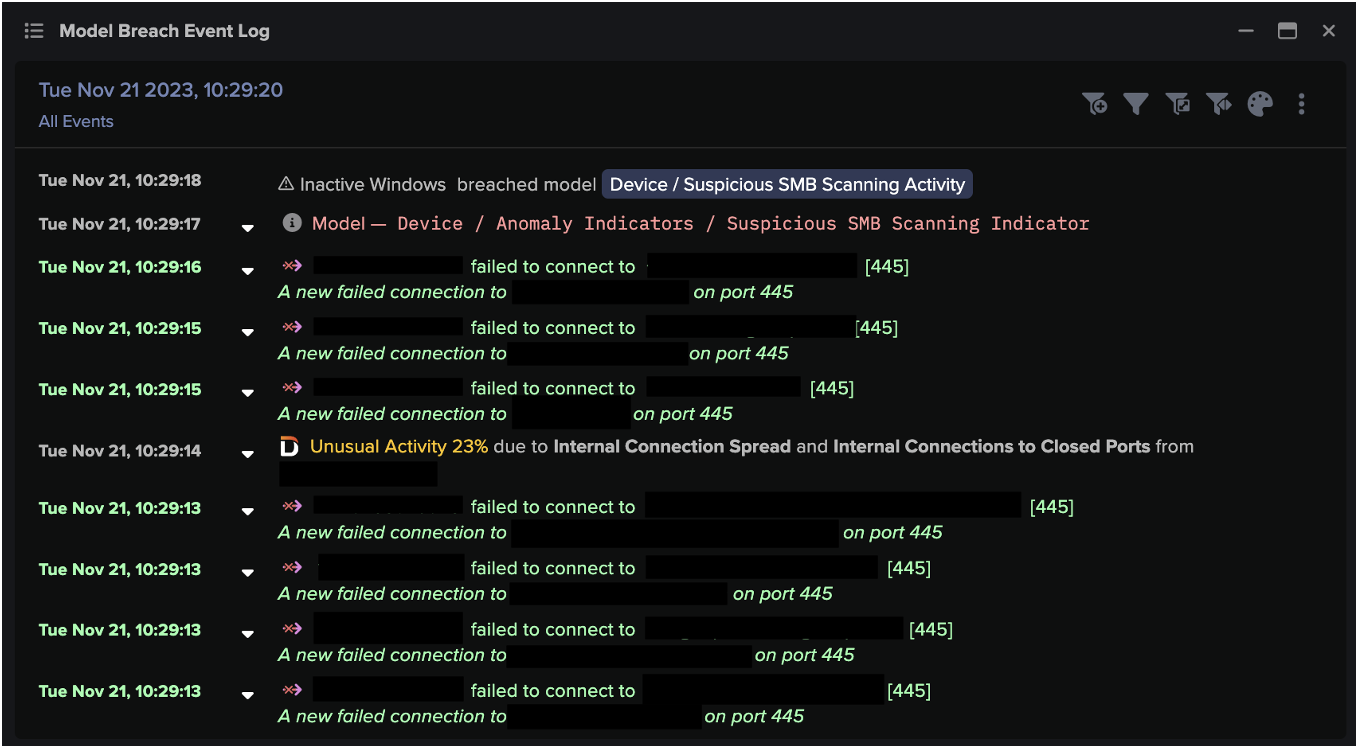
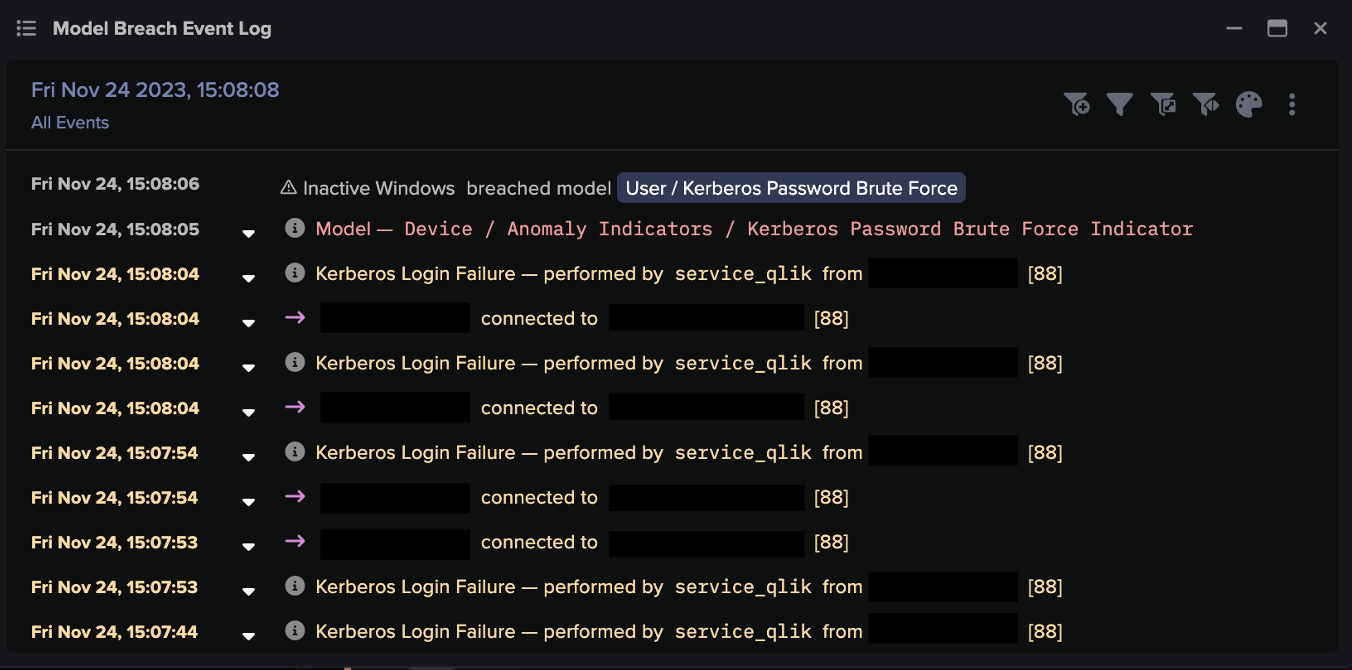
Understanding an environment and adapting to its changes is also fundamental to Darktrace DETECT: an AI-driven technology which focuses on building a comprehensive knowledge of an organization’s environment in order to spot threats the moment they appear. Because it understands what is ‘normal’ for the organization, Darktrace DETECT is able to correlate multiple subtle anomalies in order to expose emerging attacks – even those which have never been seen before. Like those essential flight instruments, DETECT offers visibility into otherwise obscure regions of the environment, and ensures that any potential problems are spotted as early as possible.
Mayday, Mayday
In aviation and security, moving quickly once a threat has been detected is critical. When an engine stalls at 3,000 feet above ground level, you don’t have time to get the training books out and start figuring out what to do. Pilots are taught to “always have an out” and be ready to use it.
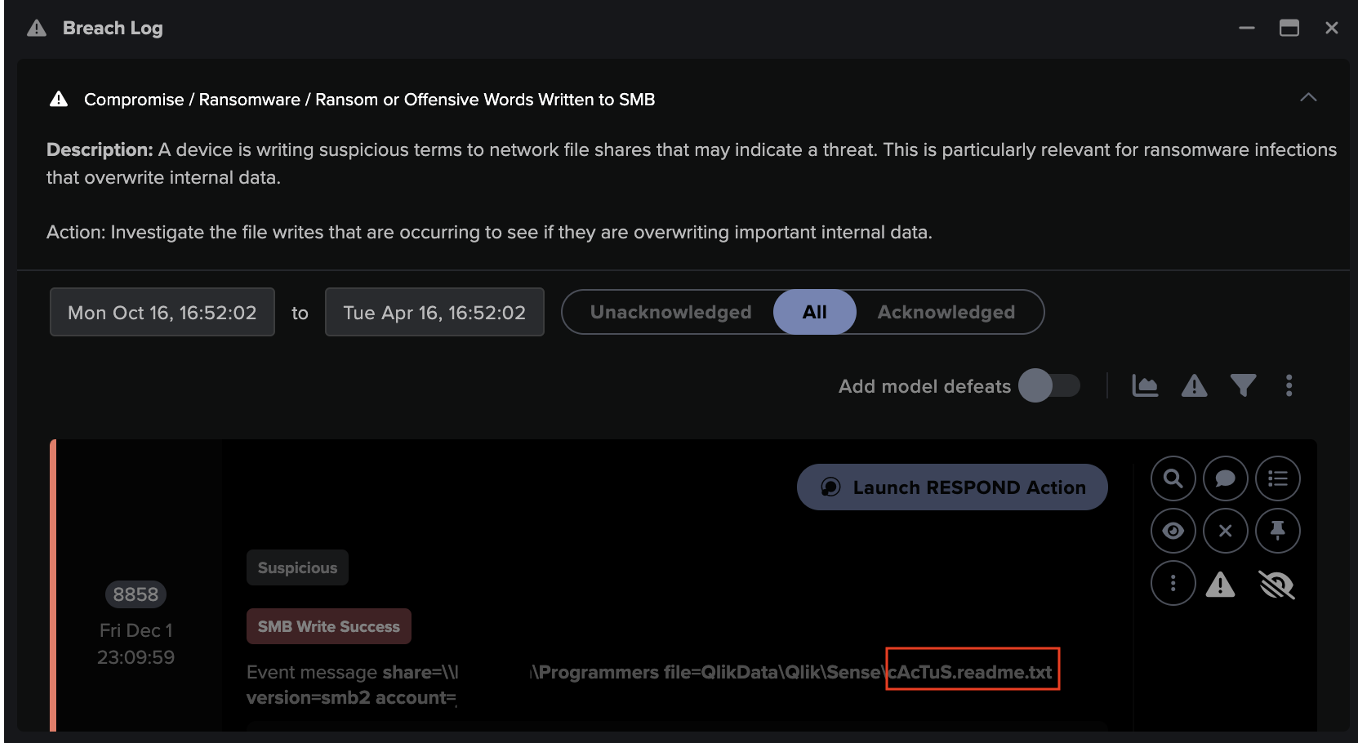
In aviation, an effective response relies for the most part on the knowledge and quick reactions of the pilot, but in cyber security, AI is making response faster and more effective than ever. Darktrace RESPOND uses DETECT’s contextual understanding in order to take the optimum action to mitigate a threat. Adaptability of this response is crucial: a single cyber-attack can come in any number of configurations, and Darktrace RESPOND is able to tailor its actions appropriately. Attacks today move too fast for human teams to be expected to keep up, but with AI taking actions at machine speed organizations can remain protected.
Always Learning
One of the best pieces of advice a pilot can take is to always be learning. Every flight is an opportunity to learn something new and become a better and safer pilot.
Darktrace DETECT, RESPOND, and PREVENT are all driven by Self-Learning AI, a technology which not only builds but continuously evolves its understanding of each business. This means that as an organization grows, adding more users, assets, or applications, its Darktrace coverage grows too, using each new data point to enhance its understanding and the accuracy of its actions and detections. Darktrace’s separate technologies also learn from each other. Each of the three product families continuously feeds data into the others, helping to enhance their capabilities and improving their ability to keep organizations secured against threats.
As cyber-attacks proliferate and increase in sophistication, they will continue to target organizations like airlines, which have large attack surfaces and copious amounts of customer data, and which cannot afford to weather sustained downtime. But with AI offering effective, proactive measures and clear-sky visibility, security teams can be confident in their ability to fight back.
































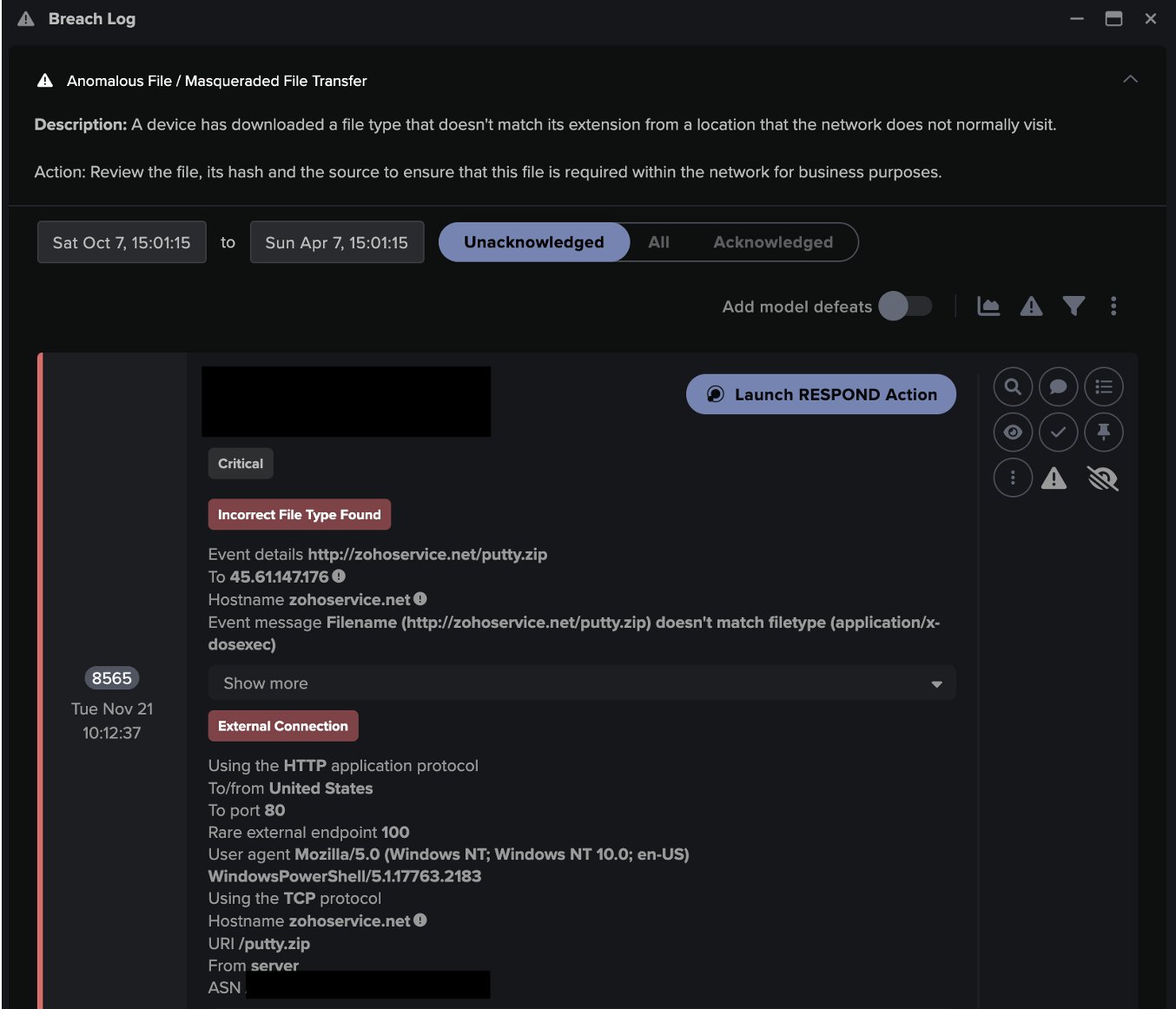
![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)