What is Admin Credential Abuse?
In an effort to remain undetected by increasingly vigilant security teams, malicious actors across the threat landscape often resort to techniques that allow them to remain ‘quiet’ on the network and carry out their objectives subtly. One such technique often employed by attackers is using highly privileged credentials to carry out malicious activity.
This emphasizes the need to be hyper vigilant and not assume that ‘administrative’ activity using privileged credentials is legitimate. In this way, both internal visibility and defense in-depth are needed, as well as a strong understanding of ‘normal’ administrative activity to then identify any deviations from this.
In one recent example, Darktrace identified a threat actor attempting to use privileged administrative credentials to move laterally through a customer’s network and compromise two further critical servers. Darktrace DETECT™ identified that this activity was unusual and alerted the customer to early signs of compromise, reconnaissance and lateral movement to the other critical devices, while Darktrace RESPOND™ acted autonomously to inhibit the spread of activity and allowed the customer to quarantine the compromised devices.
Attack Overview and Darktrace Coverage
Over the course of a week in late May 2023, Darktrace observed a compromise on the network of a customer in the Netherlands. The threat actors primarily used living off the land techniques, abusing legitimate administrative credentials and executables to perform unexpected activities. This technique is intended to go under the radar of traditional security tools that are often unable to distinguish between the legitimate or malicious use of privileged credentials.
Darktrace was the only security solution in the customer’s stack that way able to detect and contain the attack, preventing it from spreading through their digital estate.

1. Device Reactivated
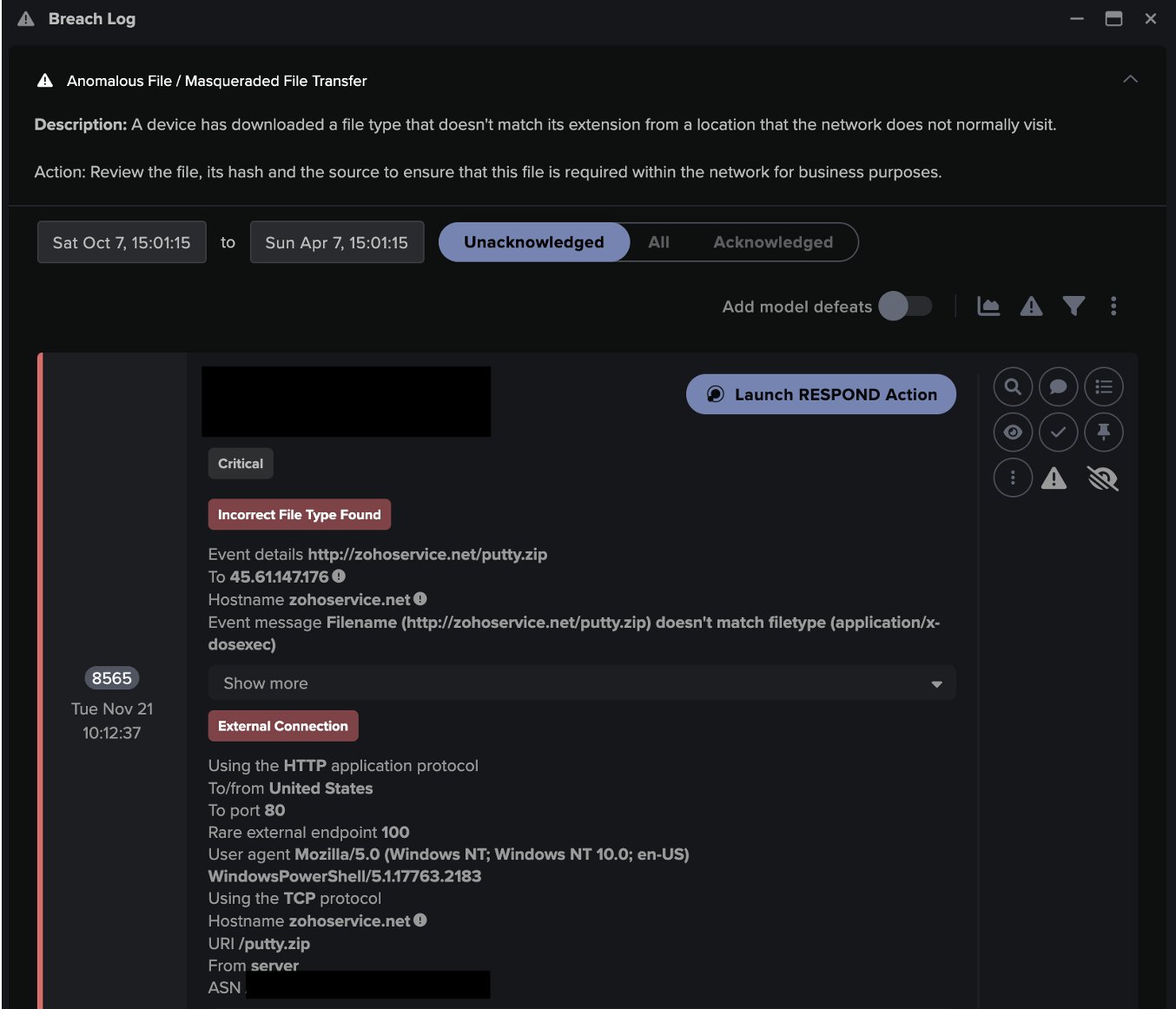
On May 22, 2023, Darktrace began to observe traffic originating from a File Server device which prior to this, had been been inactive on the network for some time, with no incoming or outgoing traffic recently observed for this IP. Therefore, upon initiating connections again, Darktrace’s AI tagged the device with the “Re-Activated Device” label. It also tagged the device as an “Internet Facing System”, which could represent an initial point of compromise.
Following this, the device was observed using an administrative credential that was commonly used across network, with no clear indications of brute-force activity or successive login failures preceeding this activity. The unusual use of a known credential on a network can be very difficult to detect for traditional security tools. Darktrace’s anomaly-based detection allows it to recognize subtle deviations in device behavior meaning it is uniquely placed to recognize this type of activity.
2. Reconaissance
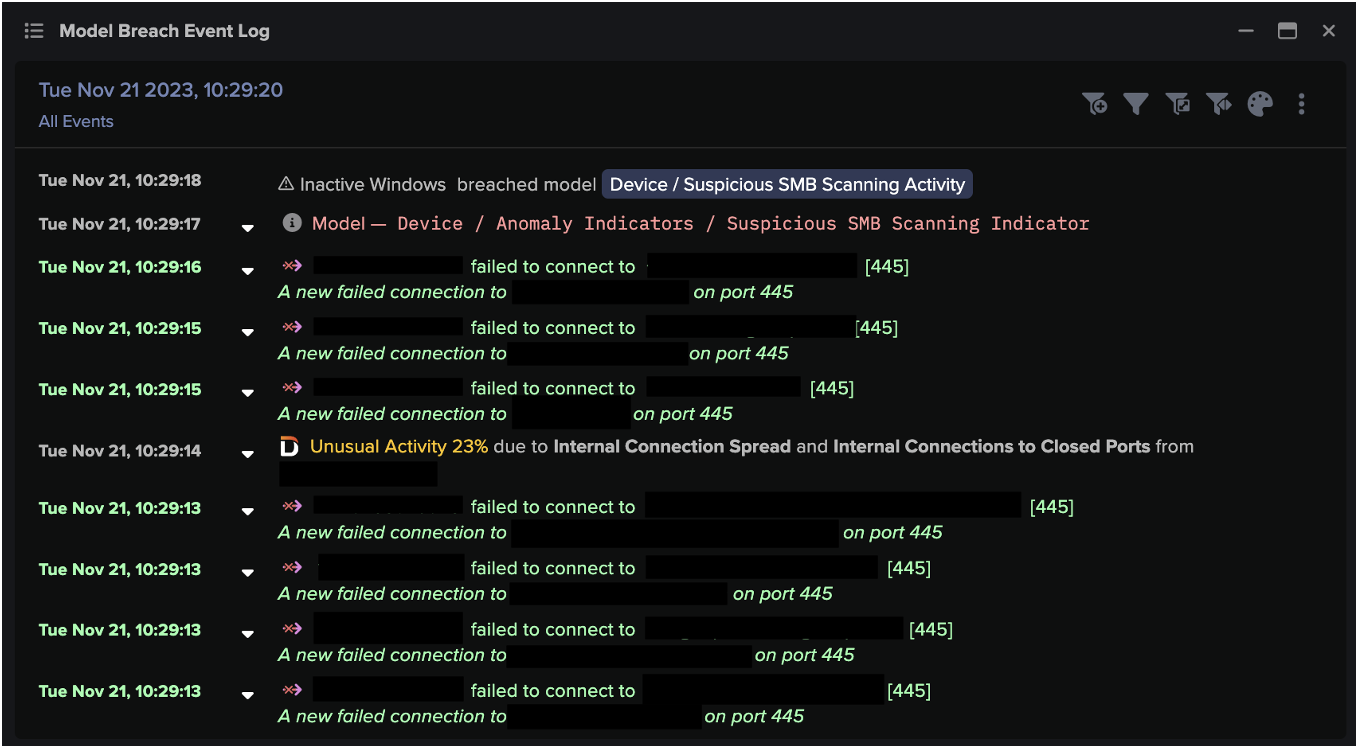
On the following day, the affected device began to perform SMB scans for open 445 ports, and writing files such as srvsvc and winreg, both of which are indicative of network reconnaissance. Srvsvc is used to enumerate available SMB shares on destination devices which could be used to then write malicious files to these shares, while Winreg (Windows Registry) is used to store information that configures users, applications, and hardware devices [1]. Darktrace also observed the device carrying out DCE_RPC activity and making Windows Management Instrumentation (WMI) enumeration requests to other internal devices.
3. Lateral Movement via SMB
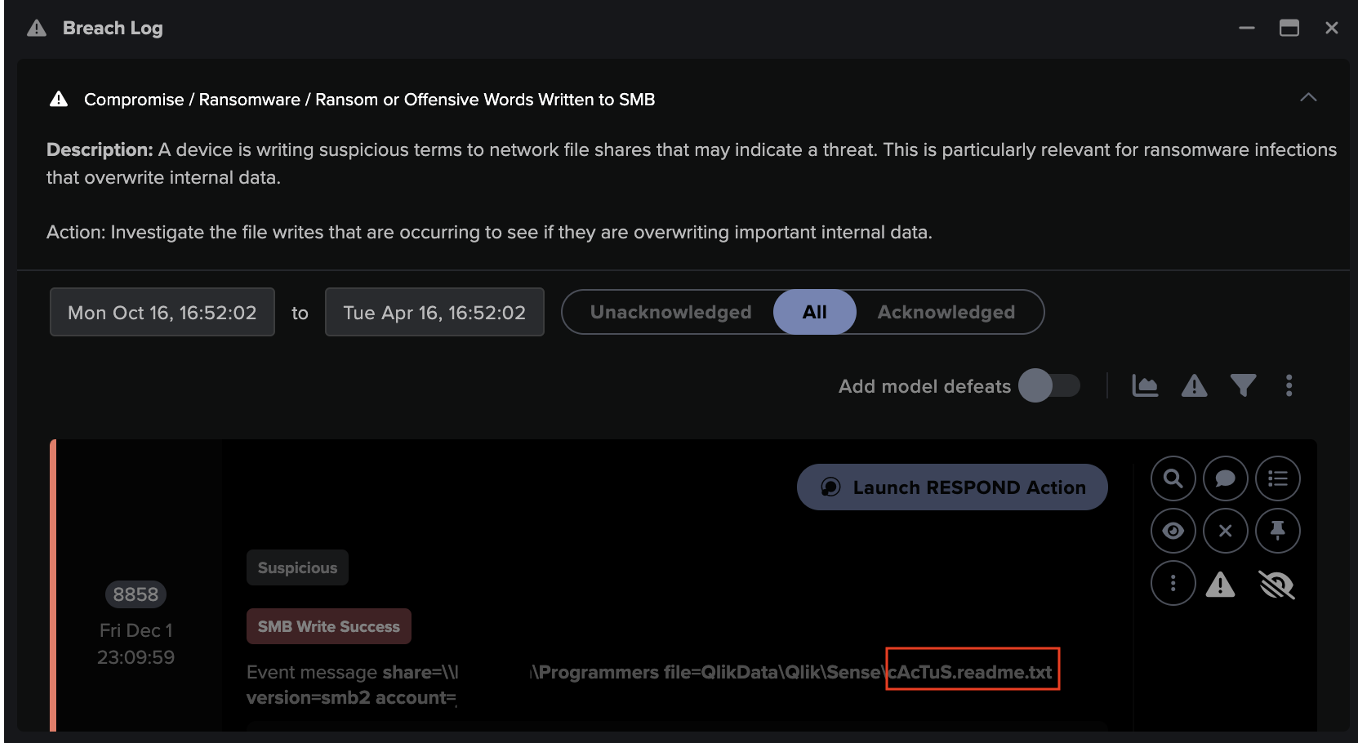
On May 24 and May 30, Darktrace observed the same device writing files over SMB to a number of other internal devices, including an SMB server and the Domain Controller. Darktrace identified that these writers were to privileged credential paths, such as C$ and ADMIN$, and it further recognized that the device was using the compromised administrative credential.
The files included remote command executable files (.exe) and batch scripts which execute commands upon clicking in a serial order. This behavior is indicative of a threat actor performing lateral movement in an attempt to infect other devices and strengthen their foothold in the network.
Files written:
· LogConverter.bat
· sql.bat
· Microsoft.NodejsTools.PressAnyKey.exe
· PSEXESVC.exe
· Microsoft.NodejsTools.PressAnyKey.lnk
· CG6oDkyFHl3R.t
5. Reconnaissance Spread
Around the same time as the observed lateral movement activity, between May 24 and May 30, the initially compromised device continued SMB and DCE_RPC activity, mainly involving SMB writes of files such as srvsvc, and PSEXESVC.exe.
Then, on May 28, Darktrace identified another internal Domain Controller engaging in similar suspicious behavior to the original compromised device. This included network scanning, enumeration and service control activity, indicating a spread of further malicious reconnaissance.
Following the successful detection of this activity, Darktrace’s Cyber AI Analyst launched autonomous investigations which was able to correlate incidents from multiple affected devices across the network, in doing so connecting multiple incidents into one security event.


6. Lateral Movement
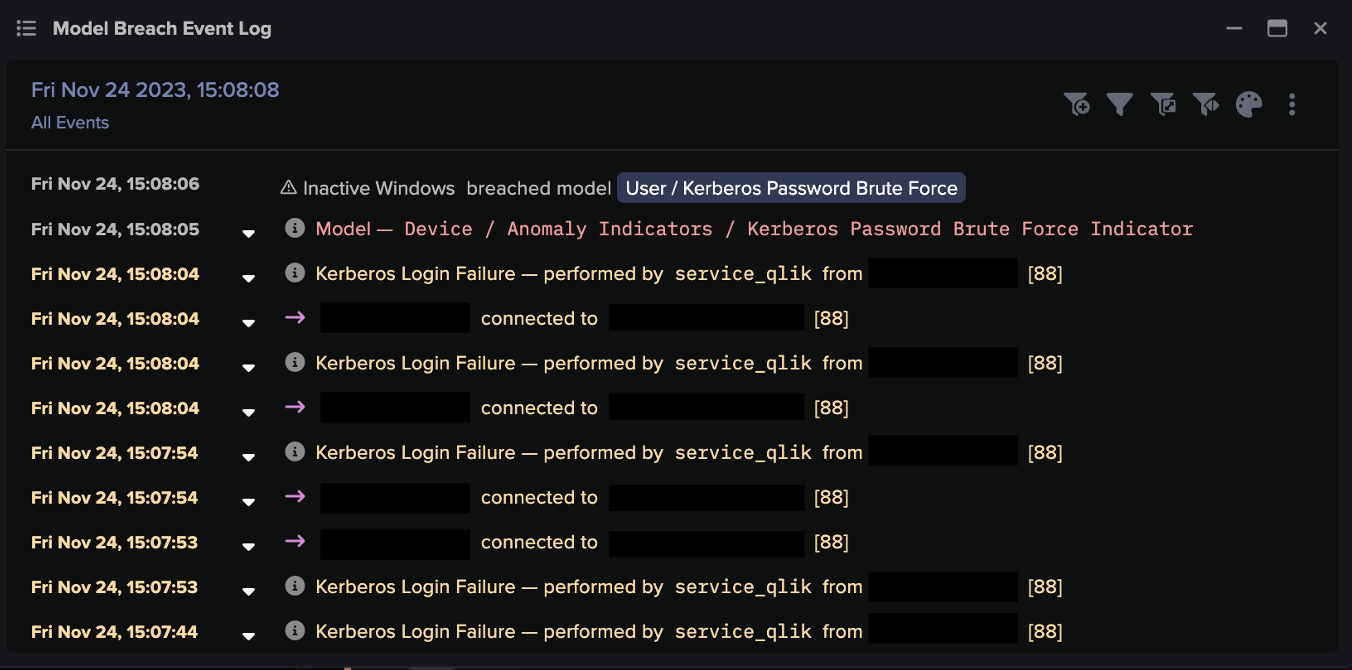
Alongside these SMB writes, the initially compromised device was seen connecting to various internal devices over ports associated with administrative protocols such as Remote Desktop Protocol (RDP). It also made a high volume of NTLM login failures for the credential ‘administrator’, suggesting that the malicious actor was attempting to brute-force an administrative credential.
7. Suspicious External Activity
Following earlier SMB writes from the initially compromised device to the Domain Controller server, the Domain Controller was seen making an unusual volume of external connections to rare endpoints which could indicate malicious command and control (C2) communication.
Alongside this activity, between May 30 and June 1, Darktrace also observed an unusually large number (over 12 million) of incoming connections from external endpoints. This activity is likely indicative of an attempted Denial of Service (DoS) attack.
Endpoints include:
· 45.15.145[.]92
· 198.2.200[.]89
· 162.211.180[.]215

8. Reconnaissance and RDP activity
On May 31, the initially compromised device was seen creating an administrative RDP session with cookie ‘Administr’. Using the initially compromised administrative credential, further suspicious SMB activity was observed from the compromised devices on the same day including further SMB Enumeration, service control, PsExec remote command execution, and writes of another suspicious batch script file to various internal devices.
Darktrace RESPOND Coverage
Darktrace RESPOND’s autonomous response capabilities allowed it to take instantaneous preventative action against the affected devices as soon as suspicious activity was identified, consequently inhibiting the spread of this attack.
Specifically, Darktrace RESPOND was able to block suspicious connections to multiple internal devices and ports, among them port 445 which was used by threat actors to perform SMB scanning, for one hour. As a result of the autonomous actions carried out by Darktrace, the attack was stopped at the earliest possible stage.

In addition to these autonomous actions, the customer was able to further utilize RESPOND for containment purposes by manually actioning some of the more severe actions suggested by RESPOND, such as quarantining compromised devices from the rest of the network for a week.

Conclusion
As attackers continue to employ harder to detect living off the land techniques to exploit administrative credentials and move laterally across networks, it is paramount for organizations to have an intelligent decision maker that can recgonize the subtle deviations in device behavior.
Thanks to its Self-Learning AI, Darktrace is uniquely placed to understand its customer’s networks, allowing it to recognize unusual or uncommon activity for individual devices or user credentials, irrespective of whether this activity is typically considered as legitimate.
In this case, Darktrace was the only solution in the customer’s security stack that successfully identified and mitigated this attack. Darktrace DETECT was able to identify the the early stages of the compromise and provide full visibility over the kill chain. Meanwhile, Darktrace RESPOND moved at machine-speed, blocking suspicious connections and preventing the compromise from spreading across the customer’s network.
Appendices
Darktrace DETECT Model Breaches
Anomalous Connection / High Volume of New or Uncommon Service Control
Anomalous Connection / New or Uncommon Service Control
Anomalous Connection / SMB Enumeration
Anomalous Connection / Unusual Admin RDP Session
Anomalous Connection / Unusual Admin SMB Session
Anomalous File / Internal / Executable Uploaded to DC
Anomalous File / Internal / Unusual SMB Script Write
Anomalous Server Activity / Outgoing from Server
Anomalous Server Activity / Possible Denial of Service Activity
Antigena / Network / Insider Threat / Antigena Network Scan Block
Antigena / Network / Insider Threat / Antigena SMB Enumeration Block
Antigena / Network / Significant Anomaly / Antigena Enhanced Monitoring from Server Block
Antigena / Network / External Threat / Antigena File then New Outbound Block
Compliance / Outgoing NTLM Request from DC
Compliance / SMB Drive Write
Device / Anomalous NTLM Brute Force
Device / ICMP Address Scan
Device / Internet Facing Device with High Priority Alert
Device / Large Number of Model Breaches
Device / Large Number of Model Breaches from Critical Network Device
Device / Multiple Lateral Movement Model Breaches
Device / Network Scan
Device / New or Uncommon SMB Named Pipe
Device / New or Uncommon WMI Activity
Device / New or Unusual Remote Command Execution
Device / Possible SMB/NTLM Brute Force
Device / RDP Scan
Device / SMB Lateral Movement
Device / SMB Session Brute Force (Admin)
Device / Suspicious SMB Scanning Activity
Darktrace RESPOND Model Breaches
Antigena / Network / Insider Threat / Antigena Network Scan Block
Antigena / Network / Insider Threat / Antigena SMB Enumeration Block
Antigena / Network / Significant Anomaly / Antigena Enhanced Monitoring from Server Block
Antigena / Network / External Threat / Antigena File then New Outbound Block
Cyber AI Analyst Incidents
Extensive Suspicious Remote WMI Activity
Extensive Unusual Administrative Connections
Large Volume of SMB Login Failures from Multiple Devices
Port Scanning
Scanning of Multiple Devices
SMB Writes of Suspicious Files
Suspicious Chain of Administrative Connections
Suspicious DCE_RPC Activity
TCP Scanning of Multiple Devices
MITRE ATT&CK Mapping
RECONNAISSANCE
T1595 Active Scanning
T1589.001 Gathering Credentials
CREDENTIAL ACCESS
T1110 Brute Force
LATERAL MOVEMENT
T1210 Exploitation of Remote Services
T1021.001 Remote Desktop Protocol
COMMAND AND CONTROL
T1071 Application Layer Protocol
IMPACT
T1498.001 Direct Network Flood































![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)