Cloud-native email security for Microsoft and google
Darktrace DETECT + RESPOND/Email
Many emails are entirely legitimate and are critical to your business, and every legitimate email is essential for understanding normal to answer determine who emails whom, tone, types of links and attachments, and other metrics.
And answer questions like has your organization ever communicated with anybody at this domain? Does the email with soliciting text appear unusual compared to previous emails?
0% being completely usual and 100% representing an email that doesn't belong in the environment.
Written to be easily understood.
When email security solutions are working, they should be invisible, working in the background to reduce risk while allowing legitimate emails to flow. Emails are protected while business flows normally.
That said, here's a glimpse at the tool belt.

.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
is it unusual for this sender or the organization?



And issues the perfect counter response for the threat.

.svg)
/Apps +
/Network
Darktrace understands a human's complete digital footprint, without reducing them to their inbox.
The complexity of humans behind the inbox are fully contextualized, making actions even more nuanced and precise.
Email communications are observed and learned to create “patterns of life” which help answer the question of whether an email belongs in the inbox. The understanding of a domain within an organization is determined by any observed domain data, which may include data outside of Email - like Network and Endpoint.
Asking questions like:
- Has anybody in the organization ever communicated with this domain?
- What do those communications look like?
- What is the typical sentiment of the emails?
.svg)
.svg)
To determine intent Darktrace/Email weighs the answers of thousands of questions and data points, like:
you might check if it's asking a user for a username and password, are there pre-populated fields, are there recognizable logos but not on their expected domains?
Malicious attachments are qualified in two key categories: Attachments containing malicious text content like links or inducement text and those containing malware.
Asking questions like:
- Does this user typically receive attachments like this?
- Does this sender typically send attachments?
- Is this attachment what it purports to be?
- Does this attachment appear suspicious?
.svg)
An example of this is the neutralization of a suspicious spreadsheet with macros enabled, it may be flattened to simply disable the macros.
.svg)
Darktrace/Email's understanding doesn't stop at your users. Learning about who they correspond with, and how, is crucial to combating potential spoofing.
Leveraging established email security techniques, like SPF and DKIM, and combining them with rich contextual information about a user, their correspondents, and their organization, Darktrace/Email is able to detect when an email is sent from a user posing to be someone else.
Darktrace/Email reveals the true sender to the end user, stopping spoofing attempts.
.svg)

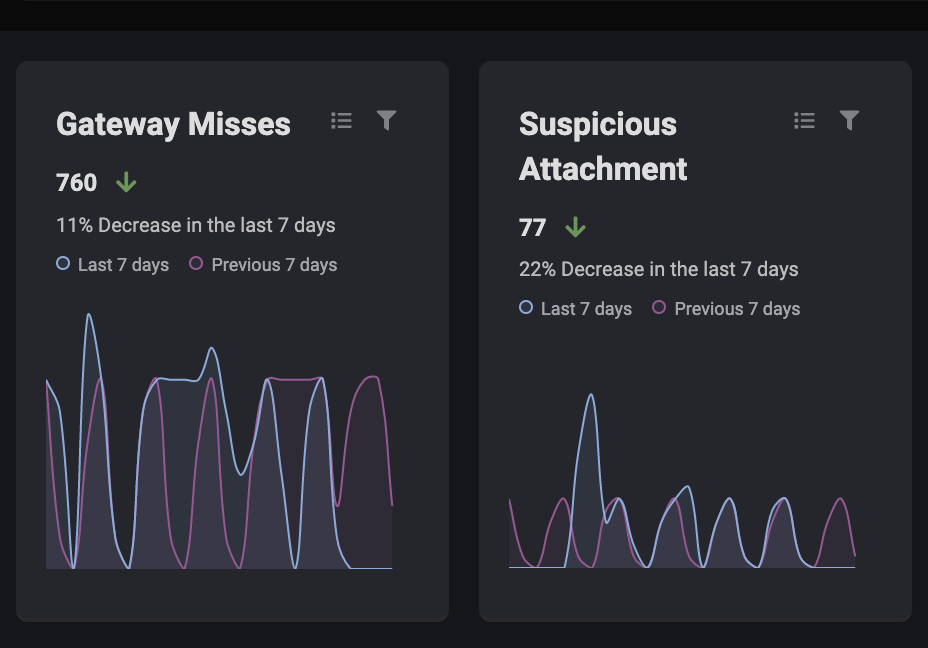
Trends you can do something with
Customizable dashboards displaying the previous 14 days of data for all the queries you value most.
Examples:
- Show me all emails that were unactioned by my gateway but stopped by Darktace/Email
- Show me emails actioned against my riskiest users
- Show me any legitimate emails my gateway moved to junk