Since its release in 2012, Cobalt Strike has become a popular platform for red teams and ethical hackers. Robust and reliable software combined with innovative features such as DNS tunnelling, lateral movement tools for privilege escalation, and PowerShell support, have made it a desirable option for organizations wanting to test their own cyber defenses. As the framework was previously only available with a commercial license, it gave security teams a distinct advantage over threat actors when preparing for attacks.
That all changed in late 2020, when a GitHub repository appeared hosting a decompiled version of the framework. Users claimed that the leaked platform did indeed function similarly, if not identically, to the commercial version, and even included a commented-out licensing check. This suddenly made the software readily available, and highly appealing for cyber-criminals: rather than requiring a paper trail and licensing, its source code was freely available for customization and use in offensive campaigns.
With sophisticated capabilities of subtle command and control (C2), privilege escalation, and lateral movement, the tools have become a favorite for ransomware gangs. Even prior to the reporting of the leaked version, 66% of ransomware attacks were found to use Cobalt Strike.
Overview of a Cobalt Strike attack
Cobalt Strike has distinctive TTPs (tools, techniques and procedures) and evasive features for each stage of the attack.

Figure 1: Cyber kill chain with Cobalt Strike
Initial compromise can be achieved with a native module for modifying emails. This includes the insertion of malicious links into existing emails or the creation of convincing spear phishing emails.
The initial payload is intentionally lightweight and can be delivered from cheaply hosted infrastructure. The smaller file size is easier to obfuscate and can be implemented in several ways, including injection into libraries or trusted processes, or creating a series of persistence mechanisms (such as turning off anti-virus prior to downloading the full payload). As such, it is remarkably difficult to detect with blocking rules or signatures.
Network reconnaissance can be done through a variety of subtle methods, using commonly used protocols such as DNS and DCE-RPC to interrogate the network. These services are frequently used in legitimate operations, so it is challenging to apply sufficiently strict controls to prevent this stage of the attack.
Lateral movement and privilege escalation are easily accessible with pre-packaged versions of common attack tools such as Mimikatz. They can interrogate an Active Directory (AD) or steal credentials, while also using SMB pipes for peer-to-peer C2. There is little space for perimeter-based security controls to monitor and restrict these abuses, even if sufficiently granular controls could be imposed.
Payload execution is a straightforward matter as Cobalt Strike beacon allows the delivery of effectively arbitrary payloads, including portability for ransomware. As the previous evasive steps can afford the attacker privileged credentials, the deployment of such payloads could look like non-threatening administrative behavior.
AI detections
Initial compromise
Cobalt Strike has utilities for creating spear phishing documents. As email remains a prolific source of perimeter breaches, threat actors will frequently implant the tool through phishes.
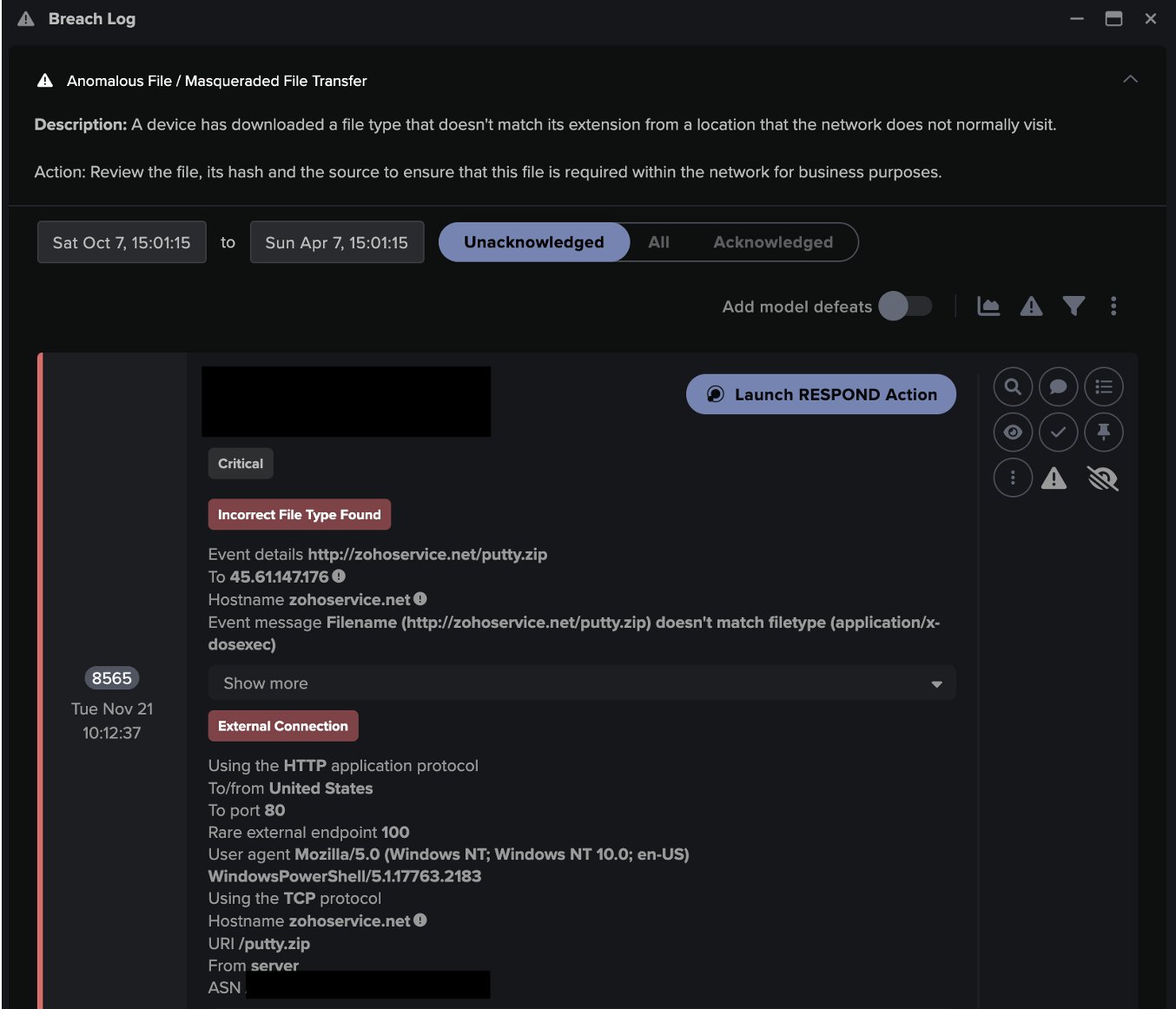
One such example was detected by Darktrace’s AI at Canadian manufacturer in June 2021. The compromise started when an end user appeared to open a phishing document, evidenced by connections to Adobe and VeriSign shortly prior to an HTTP connection to a rare external IP address.
A packet capture of the anomalous connection revealed the creation of an object using a base64 encoded string – a common obfuscation technique. If the customer had been using Darktrace/Email, the threat would have been nullified before it hit the mailbox.
Shortly after the HTTP connection, Darktrace identified unusual use of SSL, which appears to have been leveraged to upgrade to HTTPS using self-signed certificates. The endpoint served an executable, which was later confirmed as a Cobalt Strike beacon based on open-source intelligence (OSINT). Such beacons are supported by the framework, with a variety of common C2 protocols available to the attacker.

Figure 2: Event log for ‘Patient Zero’ of a Sodinokibi infection
Darktrace’s detection was based on the anomalous nature of the connection (suspicious violations of standard SSL protocols) and not a pre-defined rule. The initial compromise was detected in a matter of minutes.
Network reconnaissance
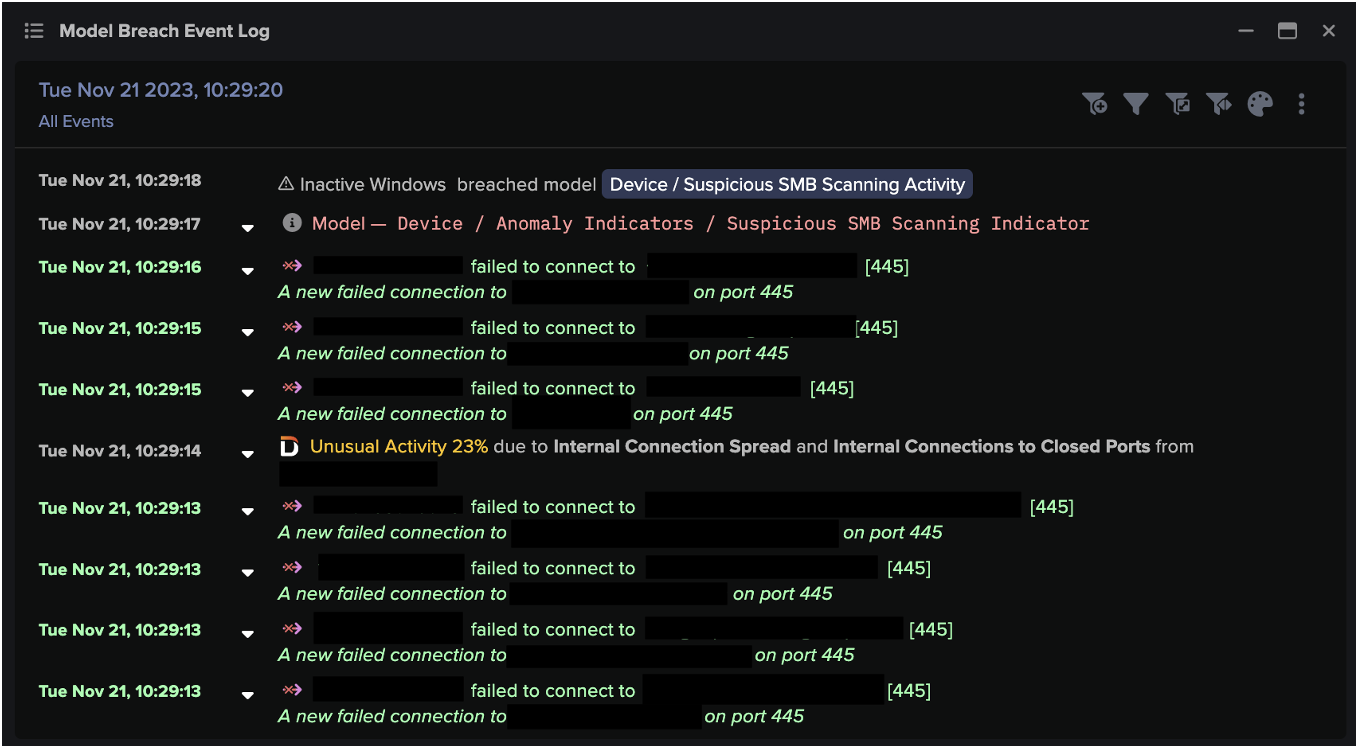
In another example at a Swiss telecommunications company in April 2021, Darktrace alerted the security team that a device – normally used for data collection – was engaging in suspicious lateral movement activity.
The host was abusing privileged credentials to perform AD reconnaissance and SMB enumeration. The alert then prompted a broader investigation, revealing that multiple devices, including domain controllers, were compromised with IoCs related to Cobalt Strike.
Thanks to Darktrace’s deep understanding of the business and recognition that this behavior was anomalous, the security team were able to remediate the infection before file encryption or large data exfiltration had occurred.
Privilege escalation and ransomware deployment
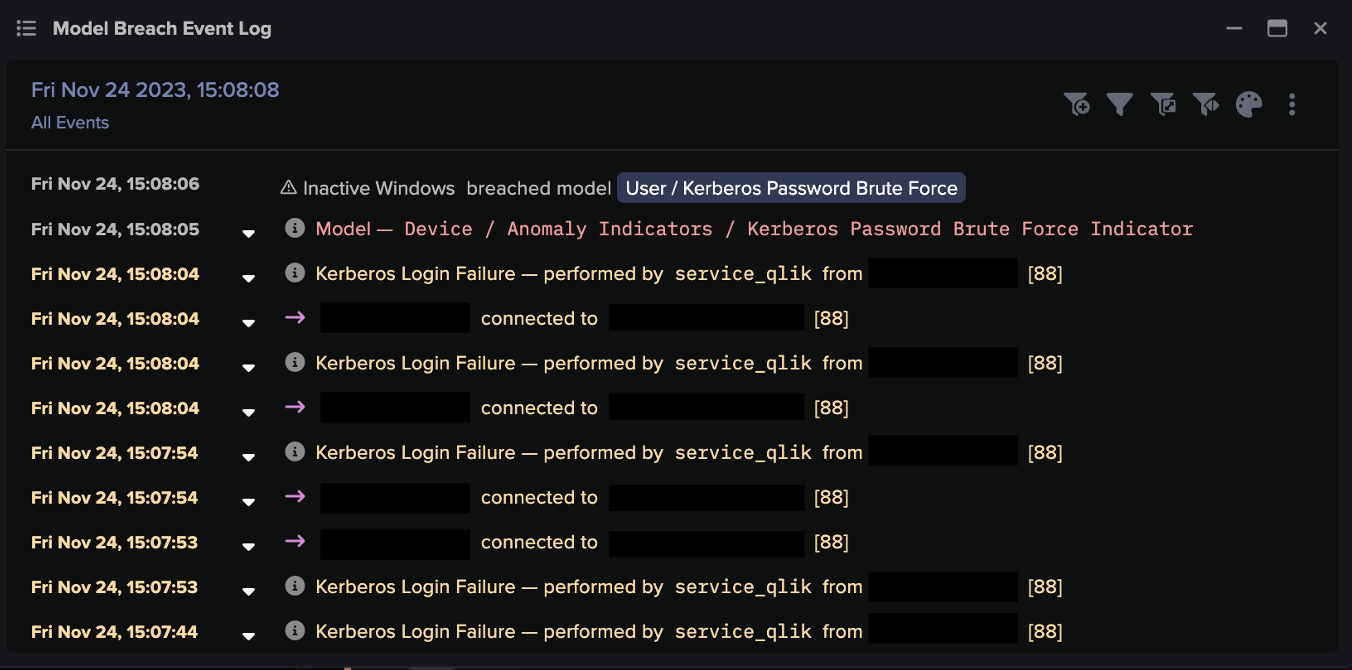
In a ransomware attack against a South African insurance company in May 2021, where a phishing email resulted in the deployment of ransomware, Darktrace first identified the creation of new administrative credentials. The devices which used the credentials were then seen making anomalous connections to various C2 endpoints associated with Cobalt Strike beacons.
Darktrace enabled the rapid identification of compromised hosts, which in turn allowed for a faster remediation and mitigated fears of a resurgent infection.
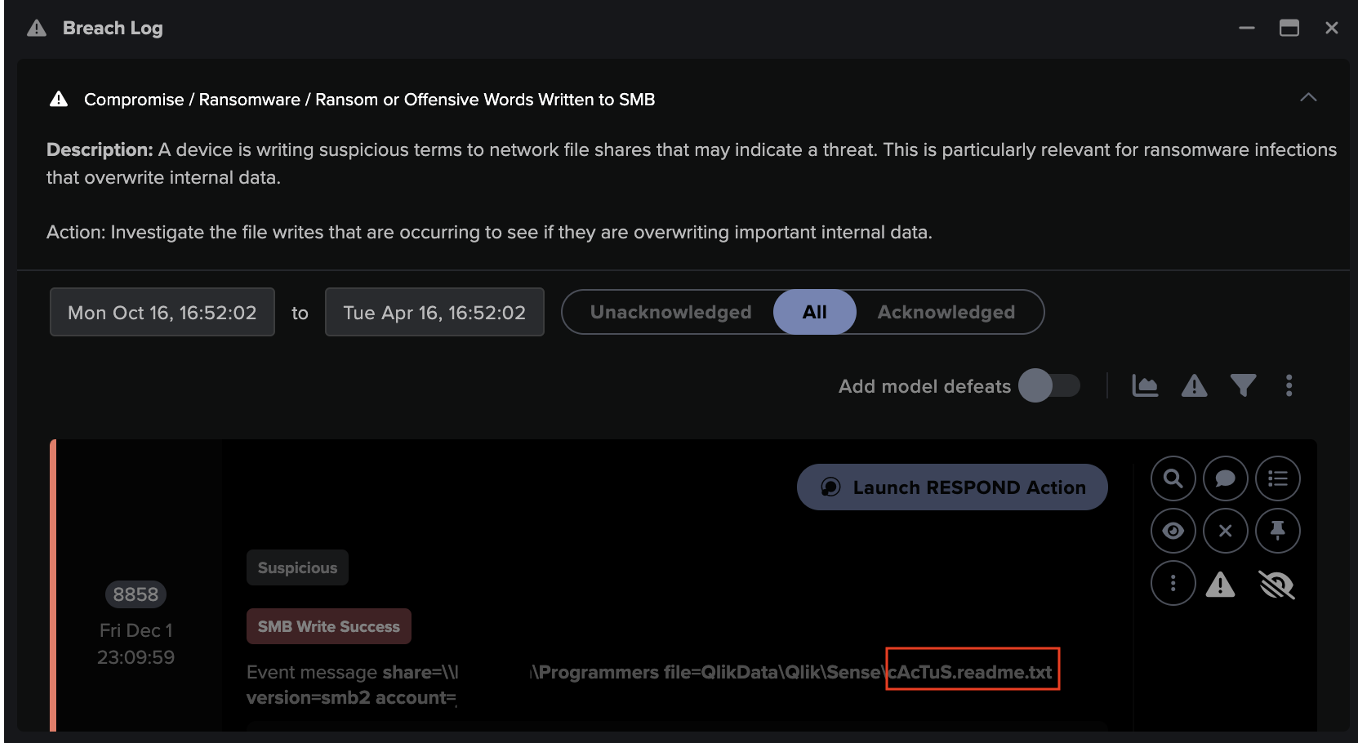
Cyber AI Analyst performed a machine-speed investigation of the activity, and automatically produced a report highlighting unusual connections on TCP port 4444 as well as other mail related ports. Port 4444 is the default port for Metasploit, another hacking platform which is often seen in conjunction with Cobalt Strike beacon. It then presented the human analysts with a full list of compromised hosts.

Figure 3: Cyber AI Analyst summary of an affected host using non-standard ports for C2 and subsequently scanning the network
Cobalt Strike malware
As it appears that a cheaply accessible analog of Cobalt Strike has been leaked, detection of the framework is critical to defend against active attackers. Signatures and rule-based restrictions prove ineffective in this regard, as the framework was designed specifically to evade such tools.
Darktrace offers the capability to detect malicious activity in its earliest stages, to triage at the speed of AI, and to autonomously block the proliferation of active threats.
Thanks to Darktrace analyst Roberto Romeu for his insights on the above threat find.
Learn how Darktrace caught APT41 leveraging Cobalt Strike
































![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)